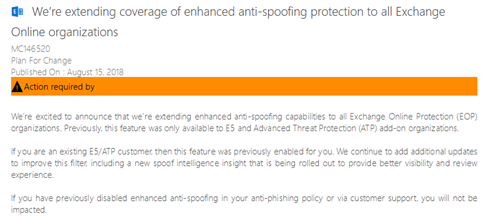
In March of this year, Microsoft released Enhanced Anti-spoofing features within Office 365 Advanced Threat Protection add-on or E5 Office 365 Plans.
Office 365 users are now receiving communication that Enhanced Anti-spoofing protection functionality will be extended to all Exchange Online Organizations.
The actual activation of the feature is scheduled for September 21, 2018.
It’s important to understand what’s the impact of the activation of this feature to avoid the effect that occurred in March when the feature was enabled on organizations protected by ATP, ie the increase in the classification of mails as “junk” .
Enhanced Anti-spoofing technology in Office 365
The first thing to clarify is that this feature raises the level of incoming mail control so the spam classification mechanism will be more restrictive, generating a larger amount of junk emails for all mail coming from inadequately protected domains.
After this change takes place, every Exchange Online organization will have access to enhanced anti-spoofing functionality that utilizes cloud intelligence, sender reputation and patterns to identify potentially malicious domain spoofing attempts. The new functionality works in conjunction with existing standard based email authentication checks (DMARC/DKIM/SPF).
Once this feature is enabled, messages that fail extended implicit authentication checks will be automatically sent to the junk mail folder.
Is it possible to use policies to customize these actions and turn this functionality on and off.
The release of the Anti-spoofing protection of March generated a bit of panic because suddenly the amount of junk mail received from users has increased significantly, involving mail from senders that until recently had been classified as safe.
Because of this, many organizations have decided to disable the feature.
I repeat that the increase in the classification of mails as junk does not derive from a problem with your mail system but derives from a low security level of the sending domain.
For this reason, it’s very important to make an information campaign for all organizations, inside and outside Office365, to adapt their mail systems to existing standard based email authentication technologies (DMARC/DKIM/SPF).
If there is still the need to disable Spoofing Intelligence, it can be done from the Office365 Security & Compliance portal:
Here you can find some documentation:
- Learn more about spoof intelligence
- Schooling A Sea of Phish Part 1: How Office 365 Advanced Threat Protection Helps Stop Spear Phishing
- Schooling A Sea of Phish Part 2: Enhanced Anti-spoofing technology in Office 365
Roberto